The default Remote Desktop (RD) Gateway encapsulates RDP in HTTPS packets listens on port 443 (for TCP) and port 3391 (for UDP). Many times you are limited to one public IP address and the port 443 is already occupied by some other service.
In that case you should change the port 443 to something else. Bellow is the procedure of doing it:
Open Remote Desktop Gateway Manager (Start > Administrative Tools > Remote Desktop Services):
- Right-click the Remote Desktop Gateway server name and select Properties.
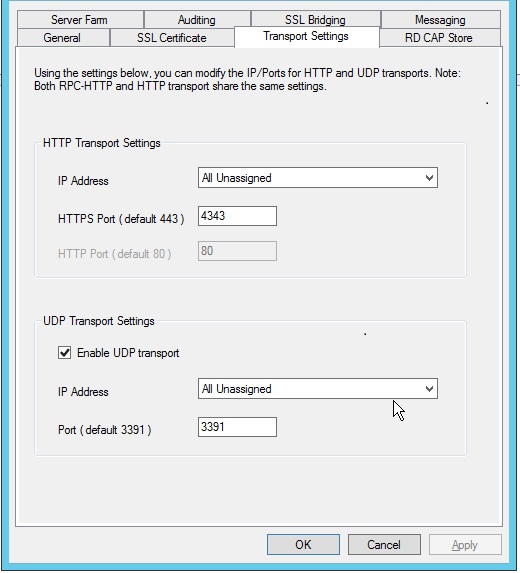
- Select the Transport Settings tab.
- Modify the HTTP and/or UDP port number and click OK.
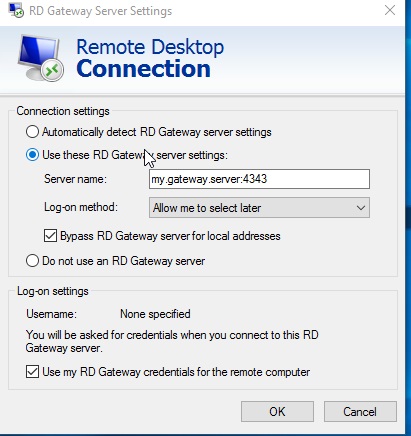
Now, when accessing with the RDP client you have to specify the RD Gateway server name with the custom port you have to specified before.
In case you are using also published Remote Web Apps you have to use a powershell trick to change the TCP port to your custom. Remote Desktop Gateway Port. On your RD Connection Broker use powershell commands below to change the published gateway to include your custom port:
Import-Module RemoteDesktop
Set-RDSessionCollectionConfiguration -CollectionName “MySessionCollection” -CustomRdpProperty “gatewayhostname:s:my.gateway.server:4343”